Configure all TLS client and TLS server settings, including TLS server certificates, on the TLS Client/Server page of the FP-I4C Web interface.
Go to the TLS Client/Server page, which has one section for the TLS client and another for the TLS server.
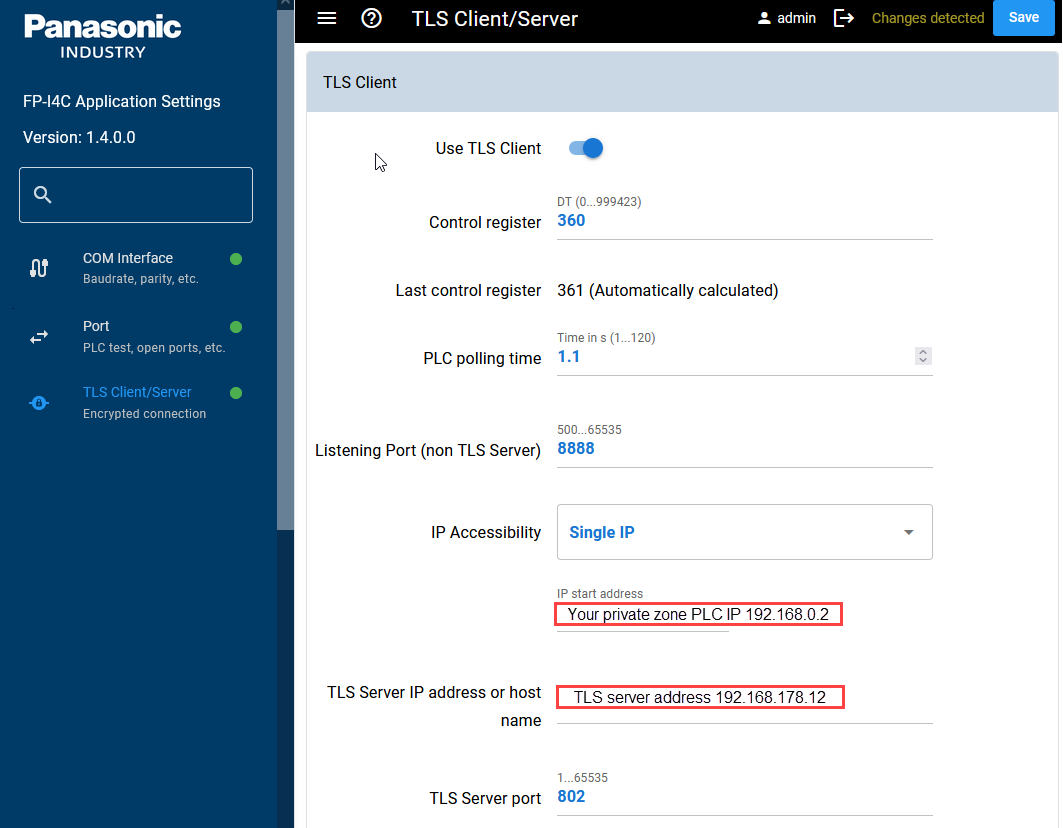
TLS client configuration
Set the client parameters as shown in the figure.
We know the IP address of our PLC and can restrict the incoming connection of the plain Modbus TCP telegrams to a single IP address.
The LAN address of the TLS server (e.g. 192.168.178.12) is our target address.
The Modbus Security default port 802 (registered at IANA) is our TLS server port.
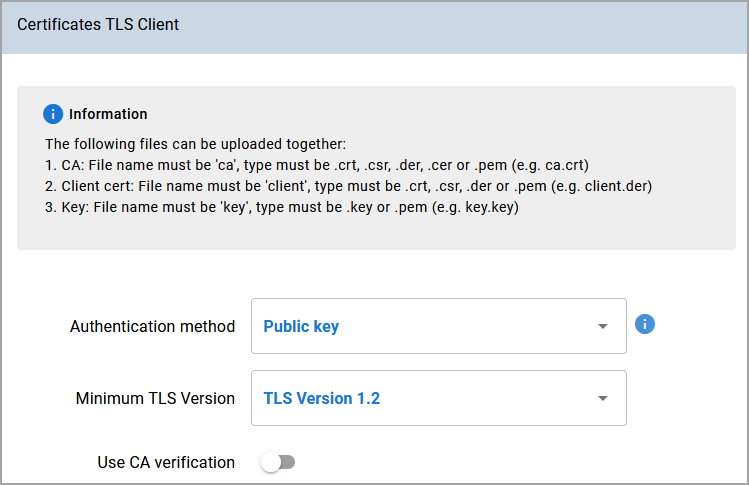
TLS client certificate
The TLS client certificates are not required and can be omitted in this sample configuration.
Select Public key and disable Use CA verification. No client certificate is needed with these settings.
This is configuration is insecure but lets you quickly set up a well running application.
In private networks Client certificate better restricts your connection.
In public networks a real CA certificate is the best choice (Use CA verification).
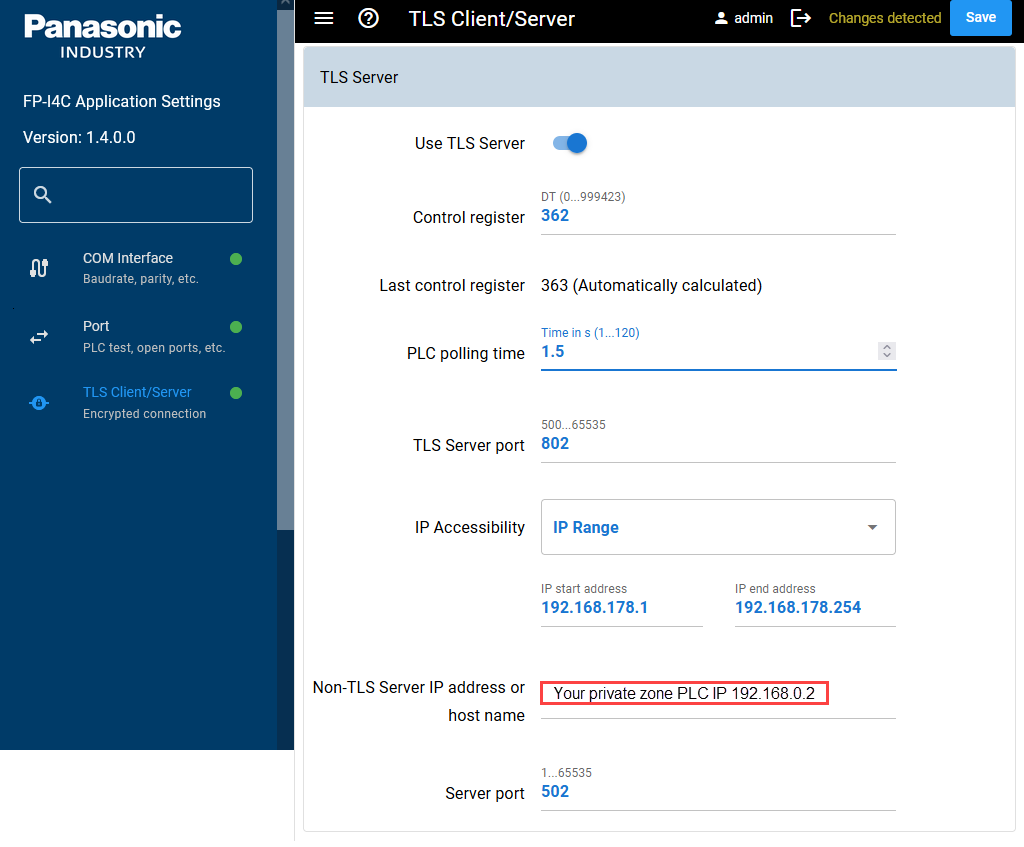
TLS server configuration
Set the server parameters as shown in the figure.
Use the Modbus Security default port as defined in the client settings.
In this example, we limit IP accessibility to our LAN.
The address of the PLC in the private zone 192.168.0.2 and port 502 are our target addresses.
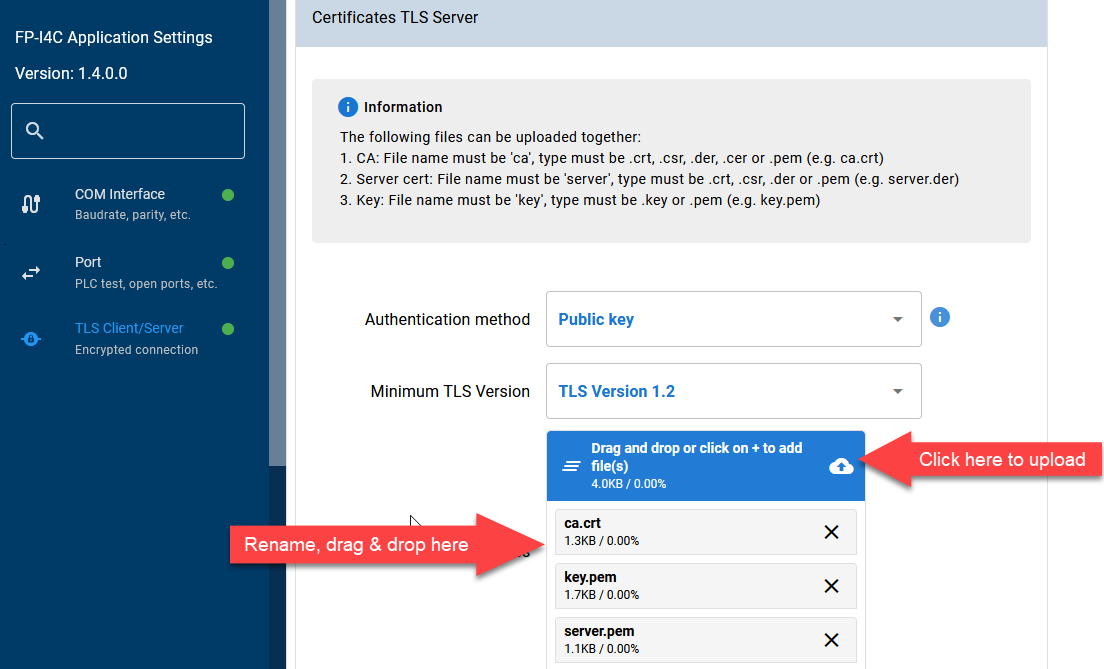
TLS server certificate
Set the parameter as shown in the figure.
The TLS server section always requires the certificate files.
The example is shipped with a test key and certificates.
Rename the files as shown in the figure.
AnmerkungThe shipped certificate files are for testing only. Using these files in real applications is insecure and dangerous! Prepare your own certificates or ask your network administrator. By renaming the files as shown in the picture you accept the risks associated with using the test files.
Now check the communication in the POU ClientTLS of your PLC program.
Don't forget to save your settings.